Guide to API Security Testing
API security testing evaluates the security of an application programming interface (API) to verify that they are protected from common threats and vulnerabilities that could compromise the confidentiality, integrity, and availability of an API and its data.
There has been an increase in the usage of APIs across various domains, such as banking, retail, transportation, and IoT. As a result, the consequences of insecure APIs can be severe, ranging from data breaches and financial losses to reputational damage and legal liabilities.

For example, early this year, T-Mobile disclosed that it suffered a data breach after a threat actor stole the personal information of 37 million postpaid and prepaid customer accounts through one of its APIs. In another API-related data breach in 2022, attackers compromised one of the largest telcos in the Asia Pacific region by scraping customer data via an unsecured and public-facing API. The stolen data included personally identifiable information (PII) of over 7 million current and former customers, resulting in identity theft and even ransom threats.
This article will explore twelve essential API security testing best practices that can help organizations improve their security posture and reduce the risk of a breach. We’ll use the popular Burp Suite security application testing tool to provide practical examples, but the principles apply across tools and platforms. Tools like Impart can be integrated with Burp Suite to streamline the security testing process by discovering endpoints, improving how Burp Suite understands the assets, and providing sample payloads for more effective and comprehensive testing.
API security testing should be positioned at multiple stages within the software development lifecycle to maximize its effectiveness. This could be at the:
- planning and design phase, which establishes security requirements early on rather than as an afterthought
- development and testing phase, which ensures developers follow secure coding practices and helps identify and address vulnerabilities, reducing the likelihood of security issues persisting into production.
- deployment and post-deployment phase, which ensures secure API configuration and continuous monitoring for security incidents, unusual activities, and threats
Regarding API security testing, organizations face a critical decision regarding their methods: manual penetration testing or automated test (CI/CD integration). Both approaches offer distinct advantages and drawbacks. Manual penetration testing, typically conducted by security professionals, provides in-depth analysis and uncovers complex vulnerabilities. However, it can be time-consuming and may impact development progress. On the other hand, automated API testing offers speed, efficiency, and early feedback. Nonetheless, it may miss security issues requiring human intuition.
To strike a balance, many organizations adopt a two-pronged approach, combining manual security testing for in-depth analysis with automated CI/CD testing for continuous monitoring and faster feedback on potential vulnerabilities in their software development process.
Summary of API security testing best practices
This table summarizes twelve essential API security testing best practices and the following sections will take a closer look at each best practice.
Twelve essential API security testing best practices
To perform API security testing effectively, you should follow a comprehensive approach covering all aspects of the testing lifecycle (including “shifting left” or “shifting right”) and the OWASP's top 10 API security risks. This section will discuss some best practices to consider when performing API security testing, including practical examples with Burp Suite.
{{banner-small-1="/design-banners"}}
Set clear objectives
Before you begin testing, you must have clear objectives for what you are trying to achieve; define the security testing objectives, scope, and expected result of each test case. A well-defined goal ensures focused efforts and thorough assessments. Understanding the different types of attacks that can be used against the APIs and the implications of each attack can also be helpful.
Below is an example of a definition of security objectives and scope for API security testing. It also highlights the tested applicable security parameters.

Identify critical assets
Understanding the functionalities and data an API handles is a crucial initial step in performing API security testing. You should determine the most valuable and sensitive resources or endpoints by identifying critical assets within your network infrastructure that could be affected by a successful attack: personal information, financial transactions, or business logic.
Here are some steps to identify critical assets within your organization:
- Review API documentation provided by the developer and pay close attention to the API endpoints, request and response formats, authentication methods, and any security-related guidelines
- Identify critical API endpoints that handle sensitive data or perform essential functions and focus initial testing efforts on these critical endpoints. Making use of automated API discovery solutions can be helpful to ensure that you capture all applicable endpoints.
Many API security solutions offer a feature that will automatically scan and generate an inventory of all API endpoints across different environments and classify them according to various criteria.
Determine test data and environment
You should use a separate test environment that mimics the production environment as closely as possible without exposing actual data or systems. This environment can be the quality assurance (QA) environment generally used for other tests (e.g., functional and performance). Your test data should also be realistic and cover various scenarios and test cases.
Assess API authentication and authorization
Various authentication mechanisms are available for API, such as basic authentication (username/password pair), API keys, and JWT (JSON Web Token). You should test how the APIs authenticate users to verify that the implemented mechanisms function as expected.
Here are some possible test cases for assessing authentication in APIs:
- Verify that an invalid username and password pair does not grant the user access to the API and will receive an appropriate error code or message
- Verify that a valid username and an incorrect password do not grant the user access to the API and will receive an appropriate error code or message
The example below uses the basic authentication method to authenticate and receive an authorization token.

An authenticated user is assigned an authorization token, which details the privileges and permissions of such a user. You should verify that the APIs enforce proper access control policies and prevent unauthorized or excessive access. Here are some possible test cases for testing authorization in APIs:
- Verify that an invalid token does not grant unauthorized access to the API’s resources or endpoints and will receive an appropriate error code or message
- Verify that a token with insufficient permissions cannot access the restricted resources or endpoints from the API and will receive an appropriate error code or message
In the example below, we created an account (testuser02) and used the authorization token to access the details of this account and a different account (kenshinsam).

We fetched data of the created account using our authorization token (in this example, the authorization token is a base64 encoding of the username and password) by appending the ID number (8) to the /user endpoint.

Then, we used the same token to gain unauthorized access to another user’s data. This exploitation was successful because the endpoint failed to perform authorization and permission checks before returning the data. This vulnerability is also known as BOLA (broken object level authorization).

Test input validation and check for injection vulnerabilities
Effective input validation is crucial in preventing injection attacks that compromise API security. You should test how your APIs validate and sanitize the data they receive from the users or clients. You should also check if your APIs reject invalid or malicious input, as is usually true in injection attacks.
{{banner-small-2="/design-banners"}}
A possible test case for testing input validation and injection vulnerabilities in an API is to send a request with a malicious SQL query as a parameter or in the body to the API endpoint and verify that the response has a descriptive message, a proper status code (e.g., 403 Forbidden) and that no data is leaked or modified in the database.
The example below shows a successful SQL injection attack that bypasses authentication.
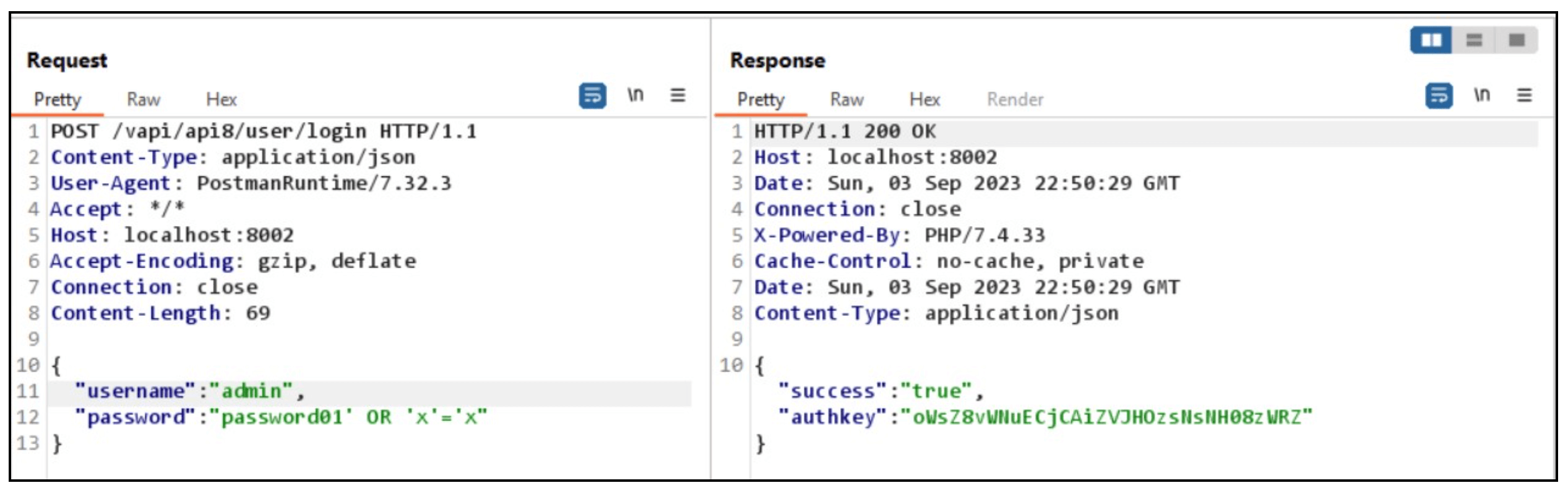
By thoroughly testing input validation and checking for injection vulnerabilities, you can improve your API’s defenses against potential exploits.
Test resilience to denial-of-service attacks
You should test how your APIs handle high-volume or malicious requests that could overload or crash them. Example security controls that can help here include API rate-limiting and throttling mechanisms that limit the number of requests per user or client.
Possible test scenarios include:
- High-volume stress testing: you can use a tool like Apache JMeter to generate concurrent requests to access the API’s performance
- Malicious payloads: you can test your payloads with requests that contain malicious or oversized payloads and monitor how your API handles them
- Rate limiting and throttling: evaluate whether your API has rate-limiting in place, test the rate-limiting mechanisms by sending requests above the defined threshold, and verify that it returns appropriate responses such as HTTP 429 Too Many Requests
Implementing rate-limiting can help prevent denial-of-service (DoS) attacks and reduce the risk of brute-force attacks. Sensitive endpoints such as /login and /submitotp are enticing to attackers and should be protected from brute-forcing.
Let us take an example of an API lacking a rate-limiting mechanism. We will use Burp Suite to exploit this vulnerability to bypass two-factor authentication (2FA).
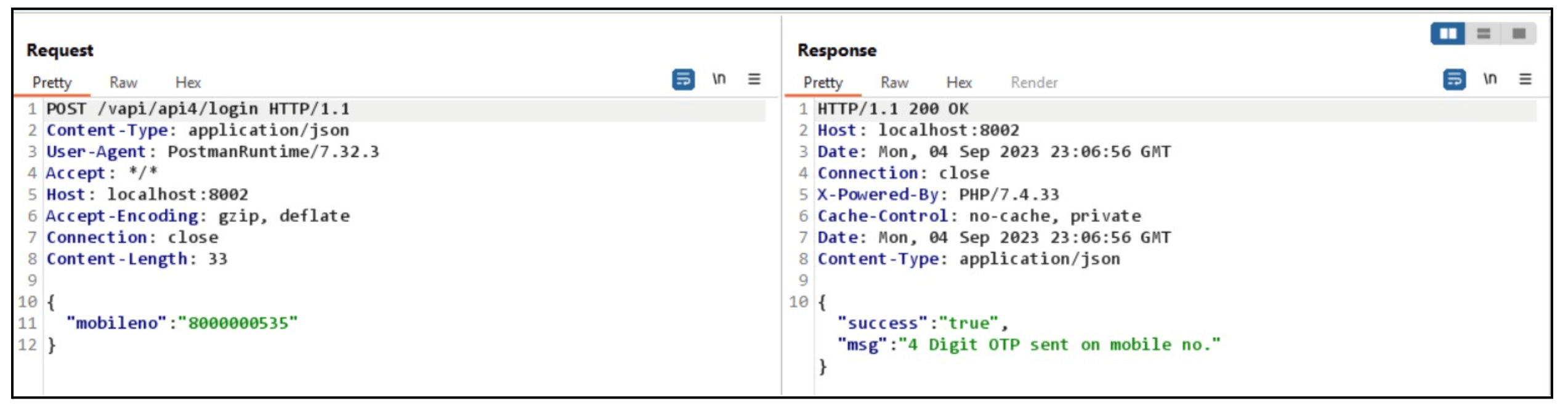
The /login endpoint sends a 4-digit OTP to the user’s phone number. However, because the endpoint lacks rate limiting, we brute-forced the OTP using Burp Suite’s Intruder module, granting us unauthorized access to the user account.

Advanced API security solutions can block attacks or use behavioral rate-limiting to limit abnormal behaviors.
Test third-party components linked to your API
You should identify and test third-party components that are integrated with or depend on your API, such as libraries, frameworks, plugins, or services. Check if these components are secure, updated, and compatible with your API. You should also test if these components introduce any vulnerabilities or issues that could affect your API's security. Timely detection of vulnerabilities in third-party packages and their dependencies using a tool like Impart Security is critical in preventing potential cyber-attacks.
Analyze error handling
You should test how your APIs handle and report any errors or exceptions that occur during their operation. You should check if your APIs return meaningful and consistent error messages informing users or clients about the problem and its cause. You should also check if your APIs avoid disclosing sensitive or confidential information in error messages, such as stack traces, database queries, or configuration details.
The error message in the example below validates that the username user01 exists in the database. This information is valuable to an attacker who can attempt to brute-force the password to gain unauthorized access.

Document your findings
You should document the results of your API security testing in a clear and comprehensive report summarizing the objectives, scope, methodology, tools, and findings of your testing. You should include screenshots, logs, or evidence supporting your findings. You should also provide recommendations or suggestions for improving your API's security.
If you perform security testing with Windows OS, you can use the Snipping Tool for screenshots and Microsoft Clipchamp for screen recordings. If testing on a Mac, press and hold these three keys together: Shift, Command, and 5 to access the Screenshot tool for screenshots and screen recordings. You can use the Gnome inbuilt application on a Linux-based system for screenshots and screen recording.
Patch vulnerabilities
You should fix any vulnerabilities or issues found during your API security testing as soon as possible. You should prioritize the most critical and severe ones and follow the best secure coding and configuration practices. You should also test your patches to ensure they work correctly and do not introduce new vulnerabilities or issues.
Educate the development team
You should share your knowledge and experience with your development team and educate them about the importance and best practices of API security testing. You should encourage them to adopt a security mindset and culture and to follow the secure development lifecycle (SDLC) principles. An example of adoptable SDLC principles is the Microsoft Security Development Lifecycle practices, as they can help developers build more secure applications by reducing the number and severity of vulnerabilities in them.
Monitor and audit
You should regularly monitor and audit your APIs to ensure they are secure. You can use tools like Splunk or ELK to collect, visualize, and analyze your API's logs and metrics and detect anomalies or incidents. You should invest in an API security solution that provides features that allow you to continuously scan and audit your API’s code and environments, detect anomalies and threats, and enforce policies and compliance standards.
{{banner-large-white="/design-banners"}}
Conclusion
In today’s ever-evolving digital landscape, APIs are essential in powering interactions between applications and users. Safeguarding these APIs demands a proactive approach.
In this article, we delved into some best practices for API security testing. While adopting these best practices in your development lifecycle can lead to functional and secured APIs, having a robust solution that incorporates and complements these best practices can improve your API security posture. Remember, API security testing is not a one-time event but a continuous and iterative process.
Contact Impart Security at try.imp.art for more API security tips and best practices and be sure to follow us on LinkedIn for the latest product news and updates.
Subscribe to our LinkedIn Newsletter to receive more educational content
Guide To API Security Best Practices
Learn how to protect customer data and improve security posture with 8 essential API security best practices.
API Pentesting Methodology
Learn how to scope an API, address the top five attacks, and report and retest vulnerabilities during API penetration testing.
API Attacks
Learn how API attacks, such as Broken Object Level Authorization, can lead to unauthorized access to confidential data and how to protect against them.
API Security Monitoring
Understand the best practices for monitoring your API, as well as some key features to look for when evaluating an API monitoring solution.
API Security Testing
Learn how to evaluate the security of an API and prevent common threats and vulnerabilities with twelve essential API security testing best practices.
API Security Tools
Learn how to use API security tools for offensive and defensive strategies, such as OWASP ZAP, Burp Suite, ffuf, Kiterunner, Postman, Swagger, and Im
API Security Solutions
Learn how to select a robust API security solution with features, best practices, and guidelines to ensure secure data exchange.
Secure API Development
Explore a detailed guide to API development with security at its core, covering the entire SDLC. Gain insights into best practices and practical tips for comprehensive API protection.
API Gateway Security
Learn how to secure your API gateway with 8 best practices, from authenticating users to rate limiting and hardening your apps.
OWASP Top 10 API
Learn how to prevent API security breaches with OWASP API Security Top 10 and implementing best practices for attack prevention.
API Authentication Security Best Practices
Learn how to implement robust API authentication security measures with best practices and example solutions.
API Discovery
Learn how to discover, document, and manage APIs for organization owners and developers with this article on API discovery best practices.
