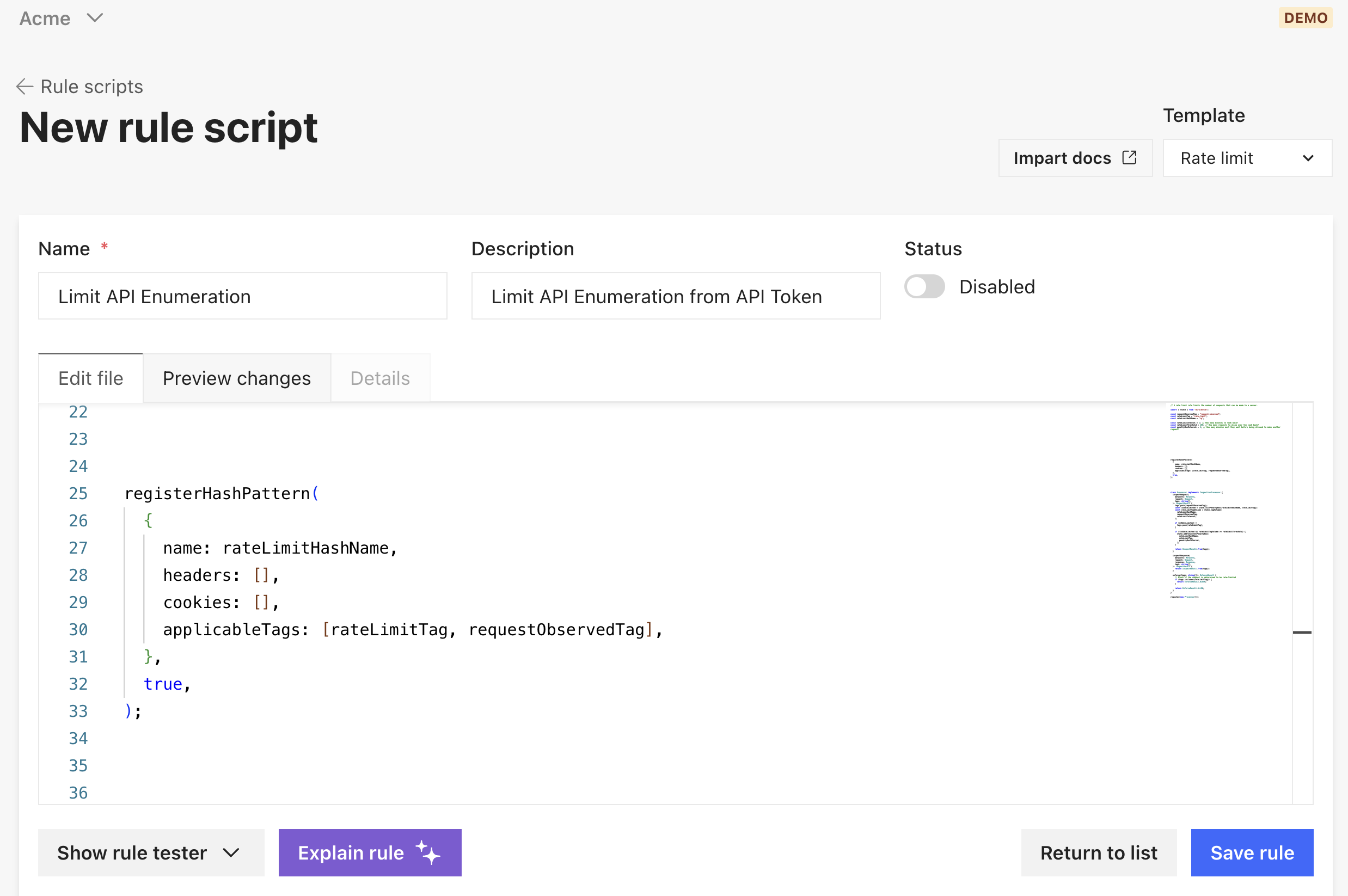
Today, we’re excited to introduce Impart Security’s Runtime Hash Patterns, an innovative feature within our Runtime Rules framework that drastically simplifies how security teams can detect and respond to different types of API users.
With the Runtime Hash Patterns interface, you can define a hash pattern for different segments of API users using any combination of user identifiers like IP address, user agent, cookies, API keys, header values, and many more.
Once a Runtime Hash Pattern is defined, any API user that matches the pattern is given a hash that can be accessed from within the Runtime Rules framework and applied to rate limiting, blocking, or enumeration rules—without ever having to expose the hash.
Unlike other API security and Web Application Firewall (WAF) solutions, which allow rate limiting on single-user characteristics and require professional services for any customization, Impart’s Runtime Hash Patterns make it easy to implement previously complex security rules, such as limiting enumeration attempts from valid API tokens or limiting automated activity from a specific user agent, IP range, or ASN.
Contact us at try.imp.art for more details and don’t forget to follow us on LinkedIn to stay up-to-date with the latest and greatest!
.svg)