Precision log generation powered by code based rules
Capture only the most relevant security data in real time, reducing noise and storage costs. Enrich the data within your existing SIEM for better threat investigation and compliance reporting.
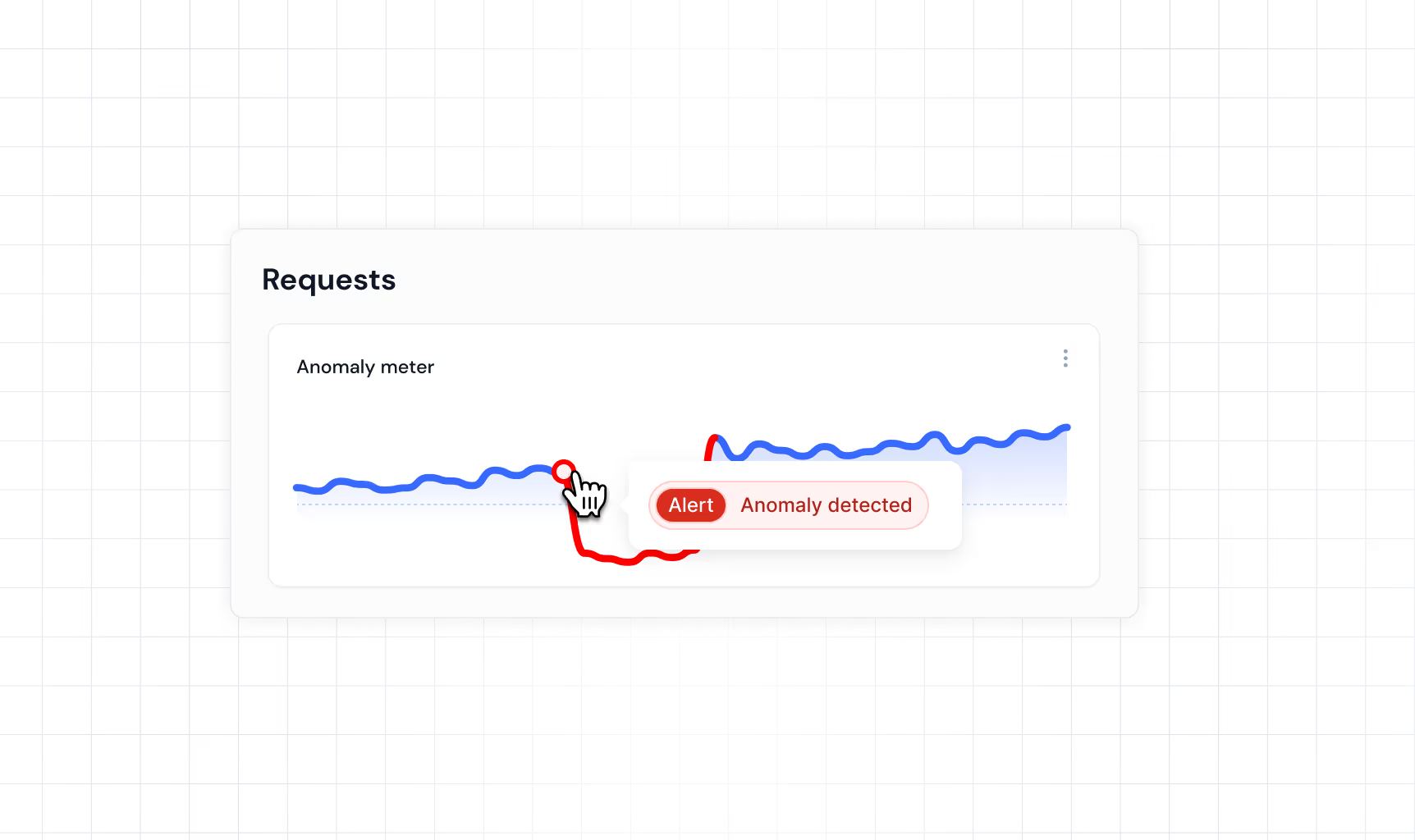
Precision logging logic
Log what matters, when it matters with precision logic logic that you can customize yourself with code based rules. Instead of logging all HTTP requests to find attackers, attack payloads, and exfiltrated sensitive data Log attack payloads, attacker identifiers, and exfiltrated sensitive data, Impart allows you to log specific pieces of each request, under specific conditions.
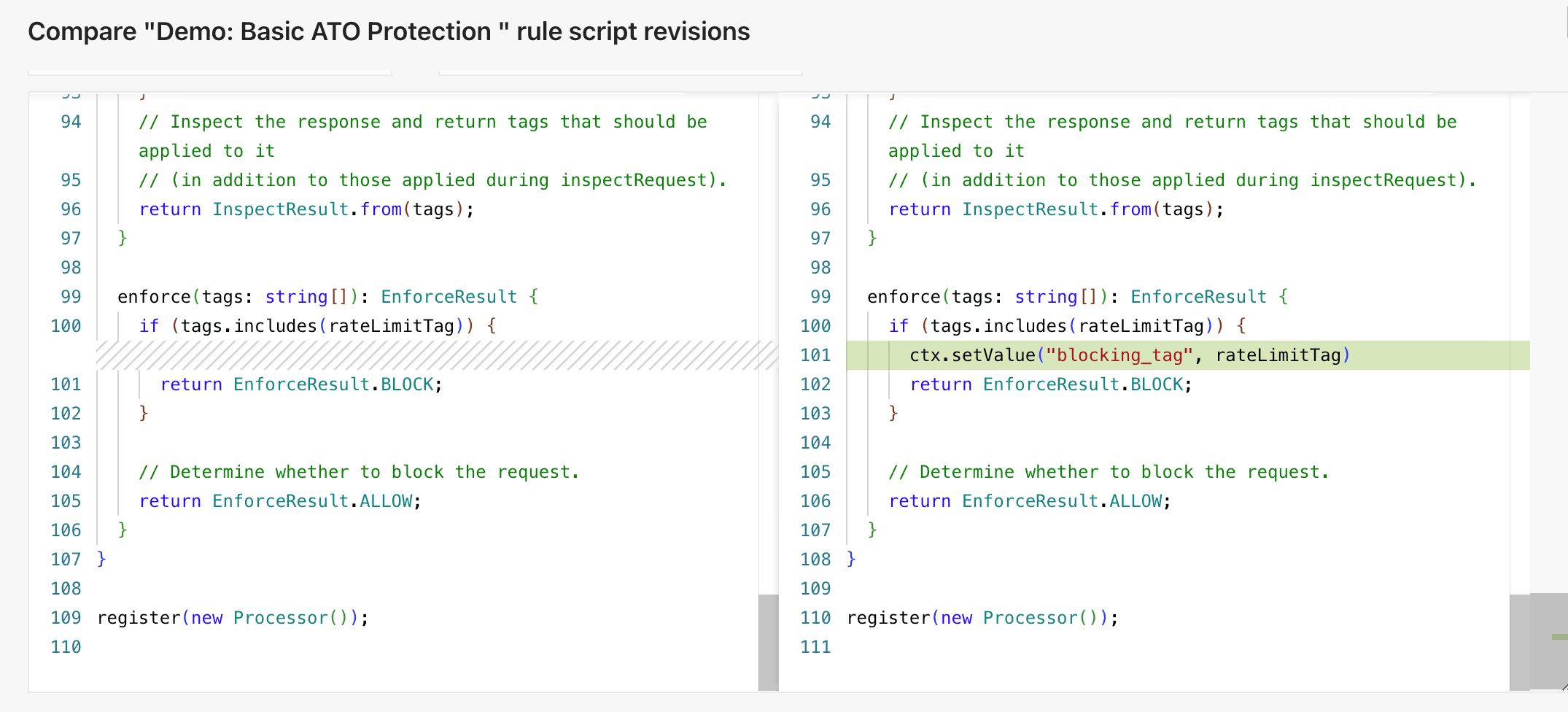
Enhance your existing SIEM
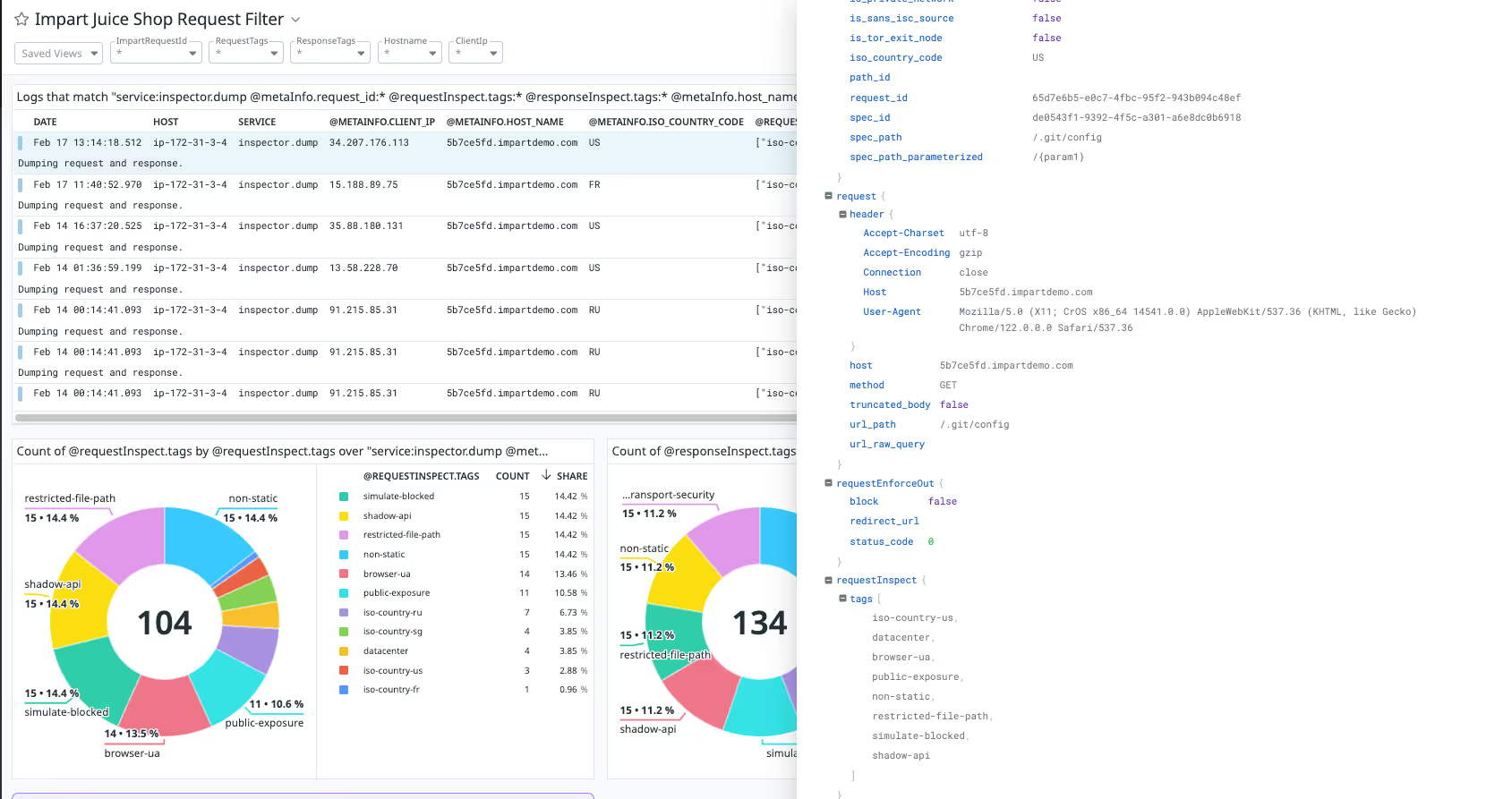
Send traffic snapshots to your SIEM in order to better investigate attacks and threats. Correlate attack payloads with other security events and enrich existing monitors and alerts with higher fidelity data for more rapid remediation.
Enhance data privacy and security
With Impart, your data stays within your own environment to ensure your privacy and compliance. Impart deploys within your environment and logs to your existing secure data pipelines, with built in, customizable redactions to ensure that sensitive data is not stored in logs.

See why security teams love us
Code-based runtime enable complete flexibility and performance for application protection at scale.











.svg)