Our security team customers have told us that JWTs are commonly used to manage API authentication and authorization. In response to customer feedback for enhanced security around these JWTs, we at Impart Security have released a few JWT-based detections into our core ruleset for more effective API security. Here are a few of the core detections we’ve released, which are available to all customers using our API security platform:
JWT Algorithm Detections
The detection for JWTs using the 'none' algorithm is a critical security measure. In some implementations of JWT, it's possible to specify "none" as the algorithm, indicating that the token's integrity is not protected by any signature. This can be exploited by attackers to forge tokens, as the server might accept these tokens without verifying their authenticity.
The detection of JWTs using the 'none' algorithm is crucial for preventing unauthorized access, as it ensures that all tokens are verified for authenticity before granting access. By flagging and rejecting tokens that use the 'none' algorithm, organizations can safeguard against attacks that exploit this vulnerability, reinforcing the security of their API endpoints.
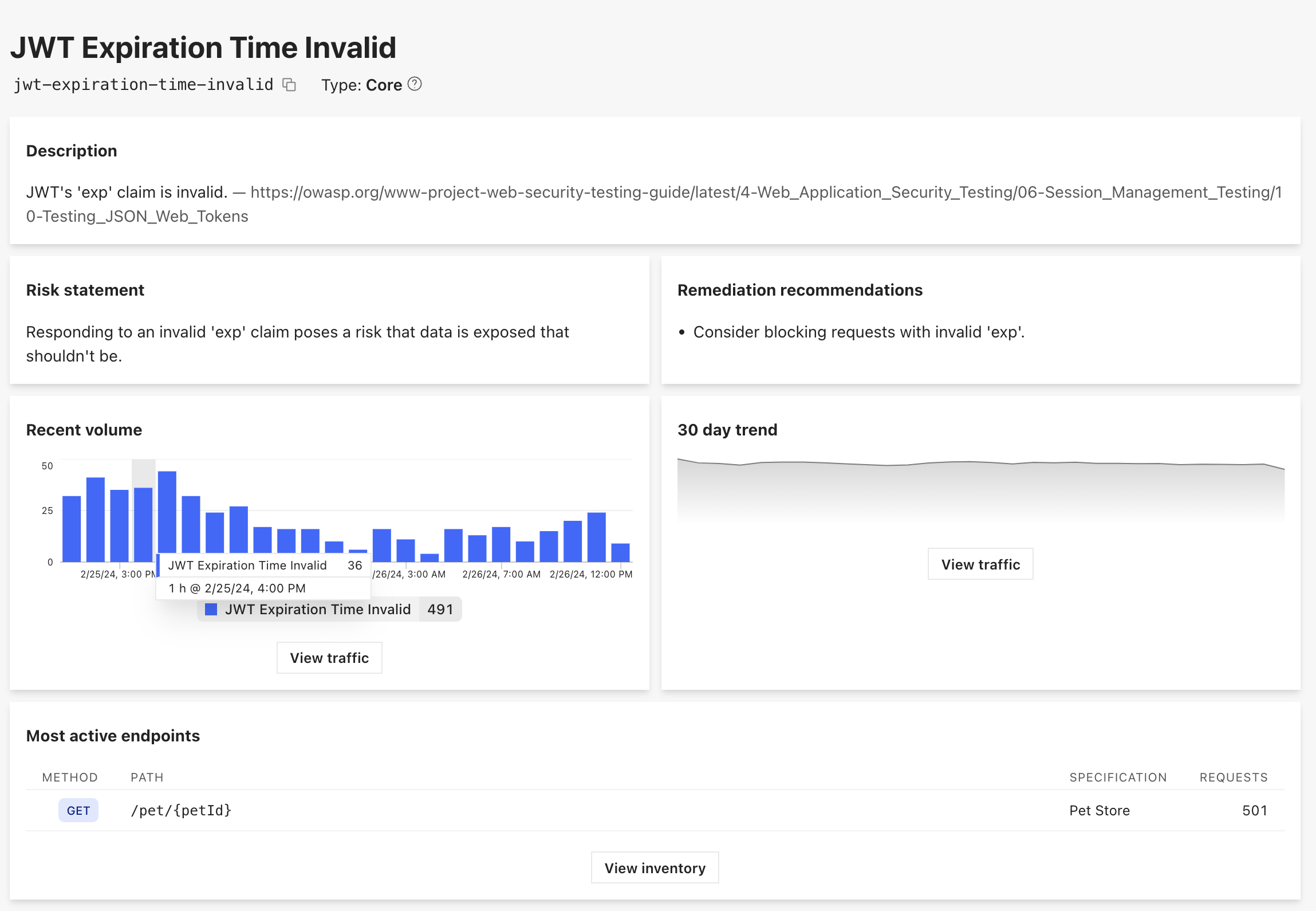
JWT Expiration Time-Based Detections
Time-based JWT detections, focusing on the 'exp', 'iat', and 'nbf' claims, are pivotal for ensuring the temporal integrity and security of token-based authentication systems. The expiration ('exp') claim detection is critical for enforcing token validity periods, preventing the prolonged use of compromised tokens by ensuring they are only accepted within their designated lifespan.
Similarly, the "issued at" ('iat') claim detection safeguards against token manipulation and replay attacks by verifying the authenticity of the token's issuance time. Lastly, the "not before" ('nbf') claim detection ensures that tokens are not prematurely used, upholding the intended temporal restrictions on token activity. These time-based checks collectively mitigate risks associated with token misuse, playing an essential role in maintaining a secure and reliable API ecosystem by enforcing strict temporal guidelines on token usage.
Non-Conforming Detections
Some token implementations encode user scopes and permissions directly into the JWT token. For these implementations, if a token requests access beyond what its encoded permissions allow, Impart can label each request with a non-conforming token scope tag with slight customizations of our existing non-conforming request and response detections in our pro-code Rule Editor.
This capability is instrumental in preventing real-world scenarios of privilege escalation and ensuring that each token can only facilitate access to resources within its authorized scope.
Combining JWT Detections with Other Runtime Rules
Impart's detections are seamlessly integrated into the customer's API infrastructure, analyzing every request in real-time. This approach not only automates the process of identifying potential security issues, but also significantly reduces the manual effort required to monitor and manage API security.
Furthermore, these detections are part of a broader suite of security features offered by Impart’s API security platform, designed to work together to create a comprehensive, adaptive security posture. When combined with other API traffic data and security mechanisms, such as rate limiting and behavioral analysis, these detections form a robust defense against a wide array of security threats.
Impart is continuing to innovate with core API security detections, ensuring that security teams can maintain the highest security standards with minimal effort.
To see a live demo of our JWT Detections and our API security platform, contact us at try.imp.art and follow us on LinkedIn to see what's new.
.svg)