Advanced Threat Detection
Protect your applications with intelligent security controls that integrate seamlessly into your development workflow, delivering comprehensive protection against sophisticated attacks while maintaining the performance and usability your team demands.
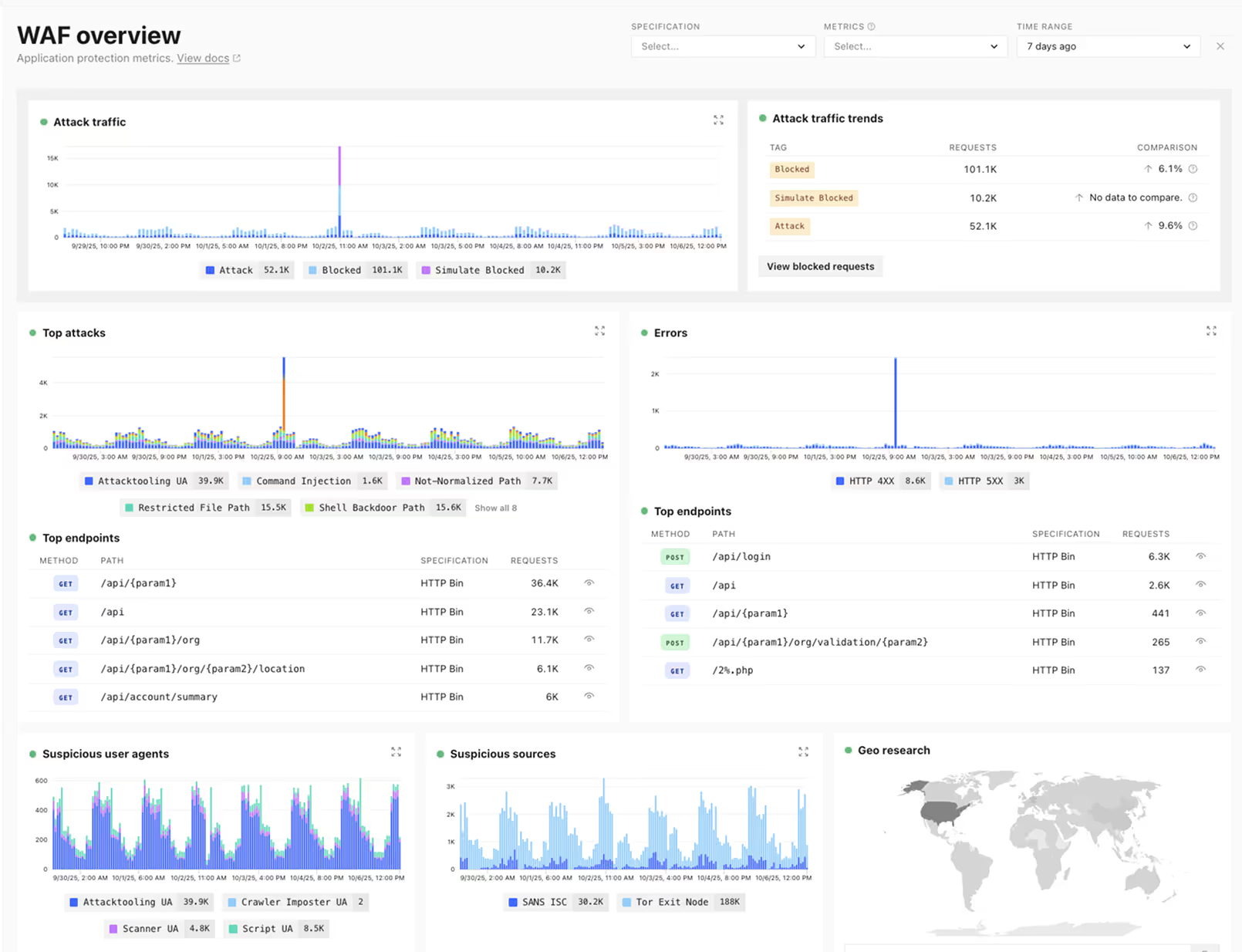
Block attackers, not customers
Target attackers not just by IP, but by any attribute in requests. (e.g. API token, authorization header, session cookie)
Avoid blocking customers by automatically surfacing normal traffic patterns that trigger false positive detections and creating granular exceptions to exclude them.
Go beyond basic, volumetric IP rate limits and detect whether attackers are actually trying to enumerate parameters - even if they are coming from many IPs.
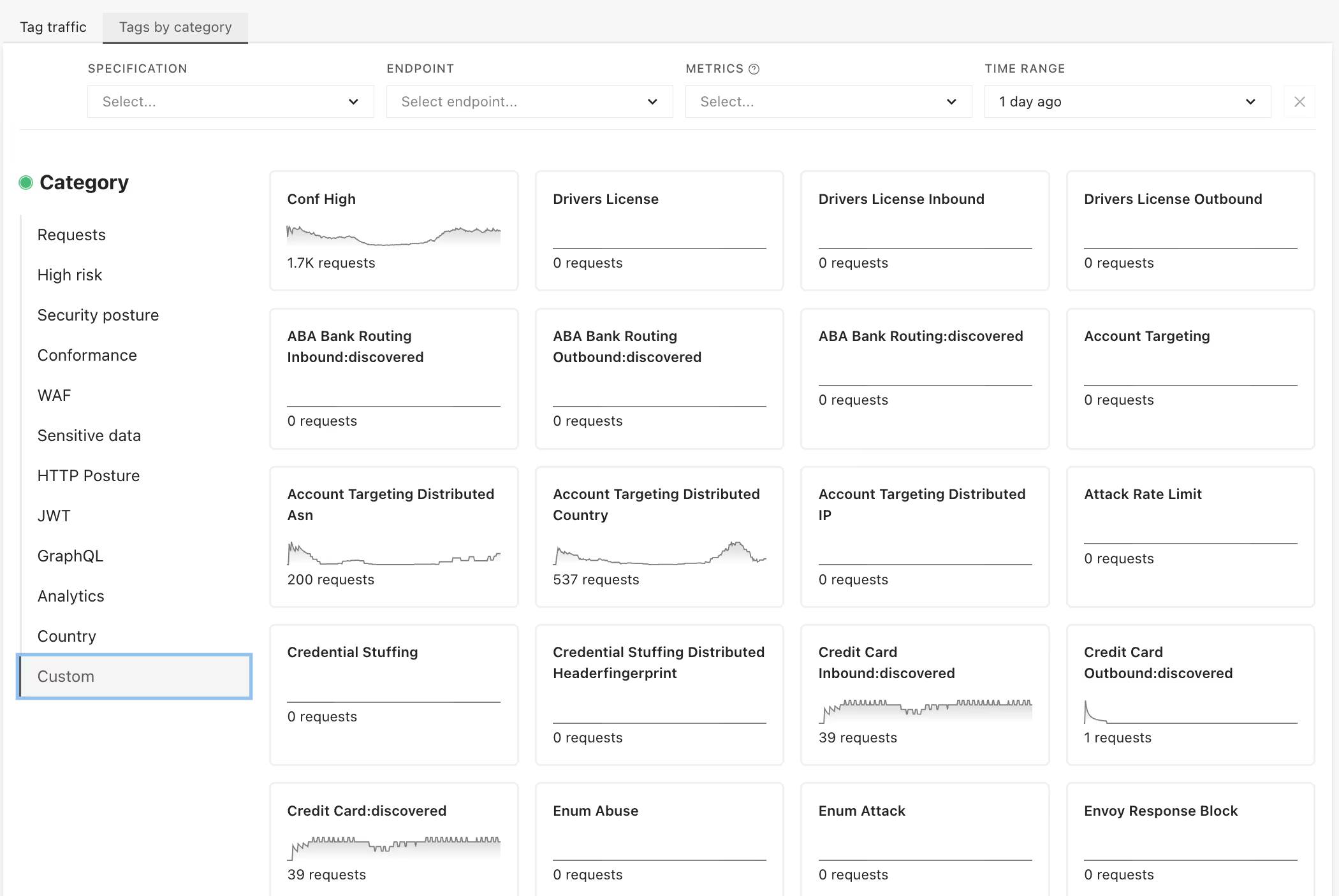
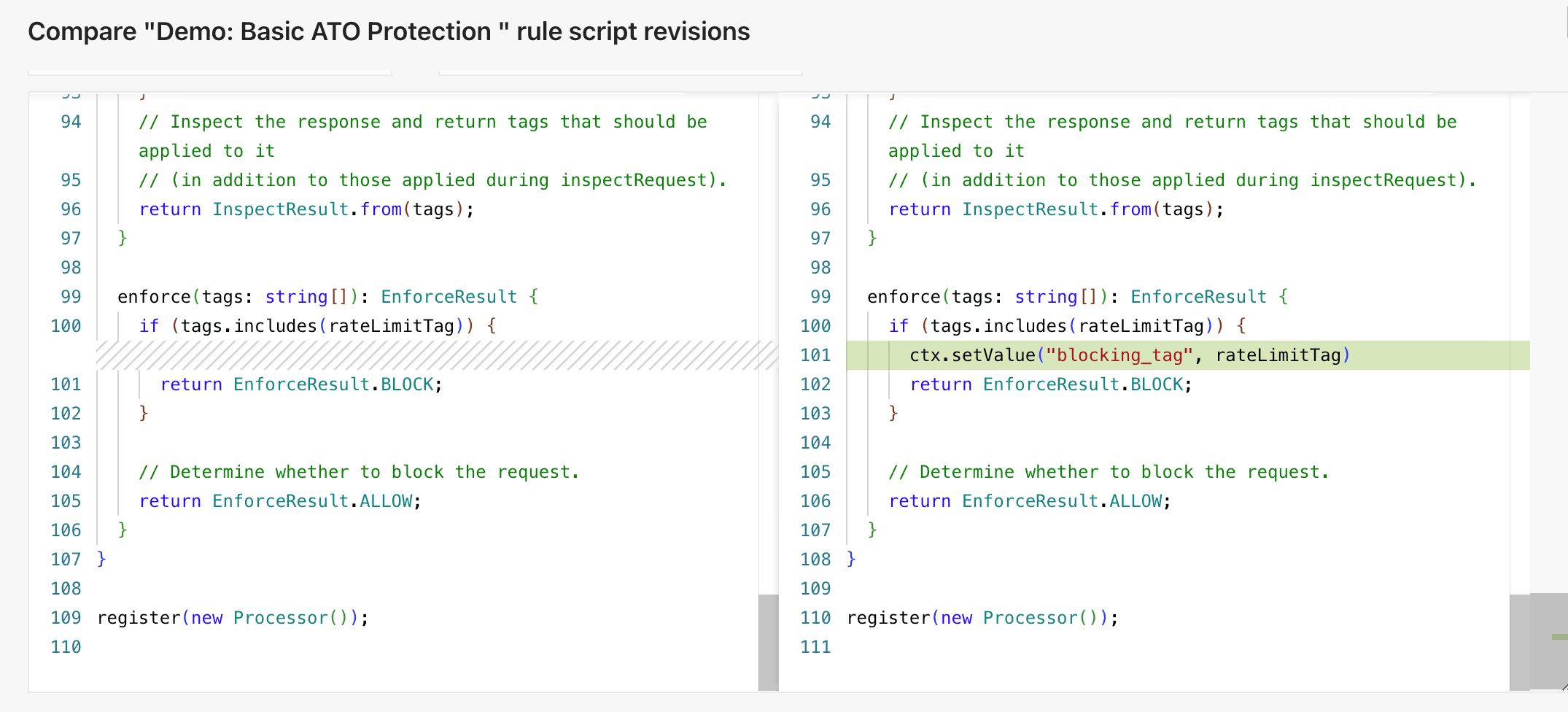
Move at the speed of code
Attackers change up tactics with the speed & flexibility of code, but traditional WAFs are constrained by click-ops and form-based rule builders.
Impart’s rules can be customized using Assemblyscript and dependencies can be managed with Rule Graphs, which makes them more flexible and extensible. They can also be regression tested before deployment, versioned, and managed with IaC tools like Terraform, making them safe to use at scale.
95% of Impart’s customers are deployed in blocking mode in production.
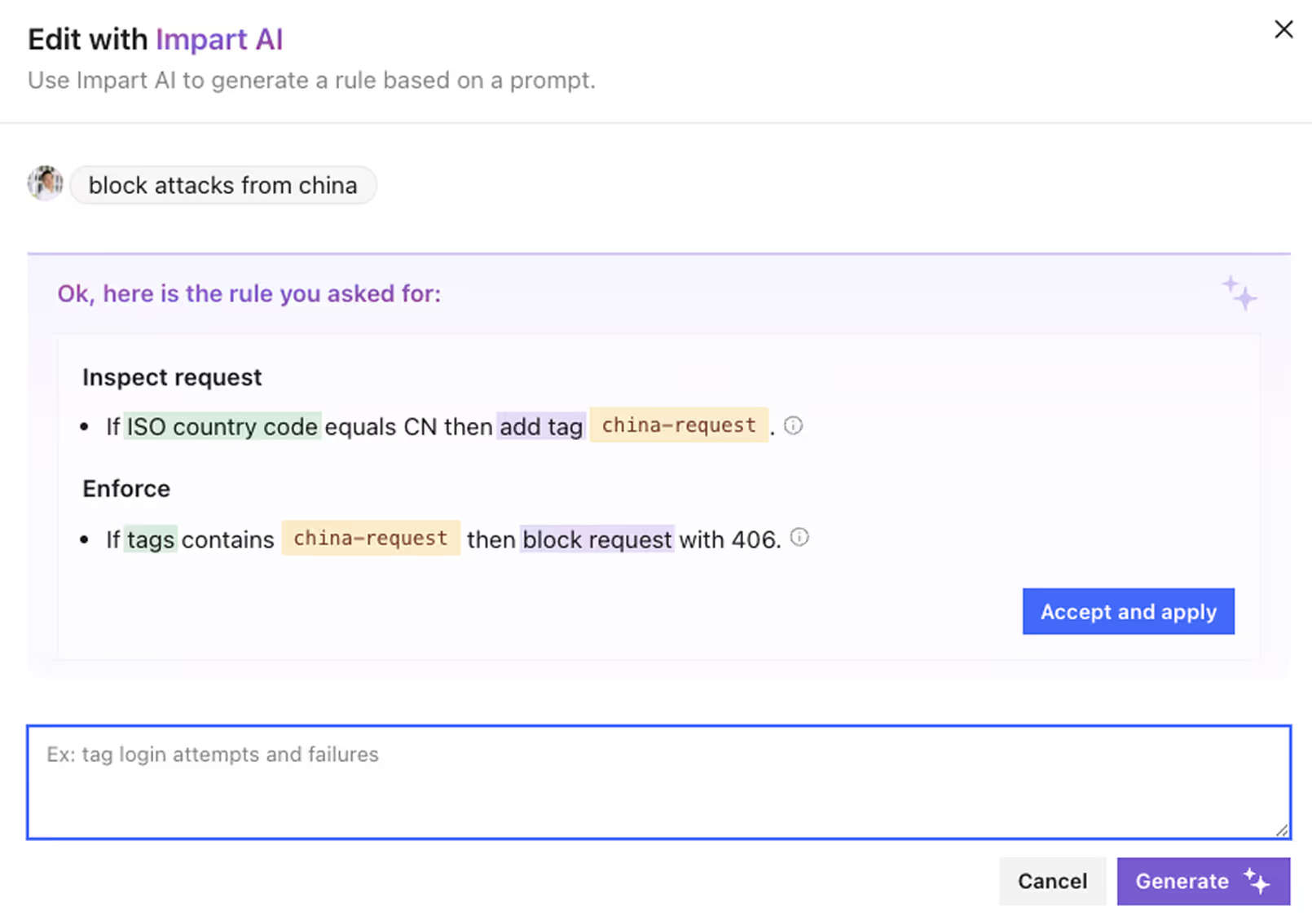
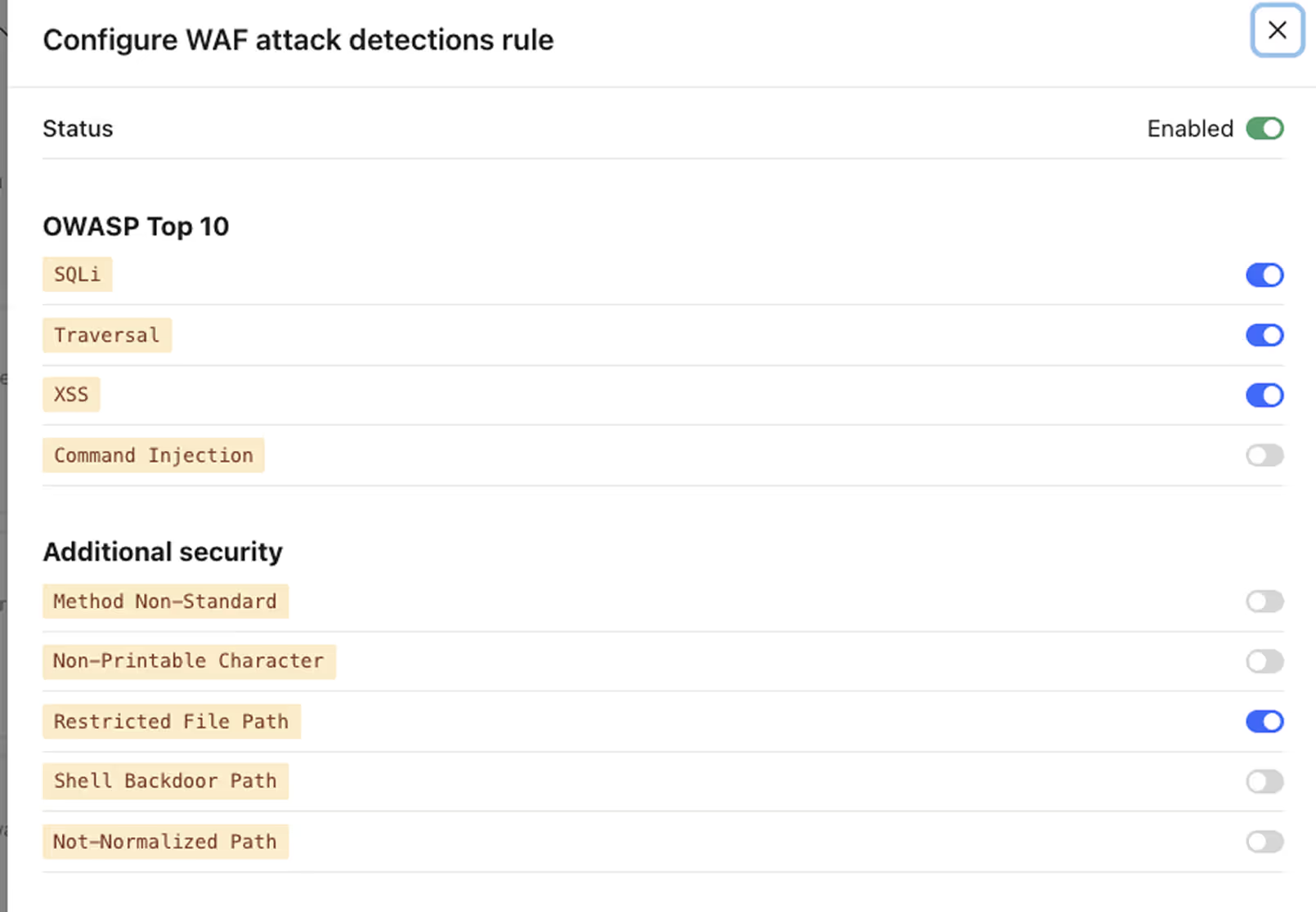
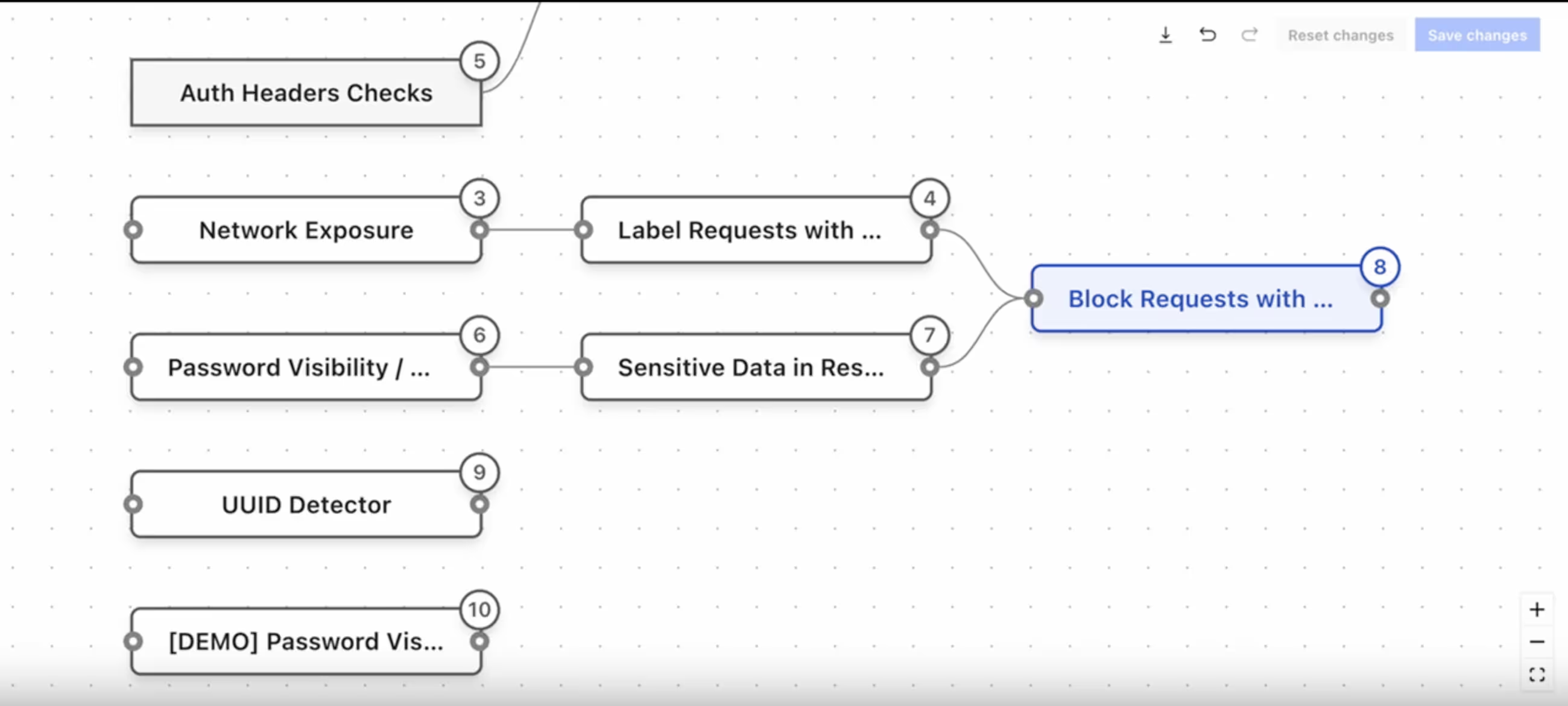
Customize detections easily
Runtime Rule Graphs enable security teams to easily drag and drop basic detections into complex policies.Unlike traditional WAFs which require specialized knowledge of regex and proprietary security languages, Impart’s Runtime Rule Graphs offers a more intuitive, flexible way to see and manage firewall rules.
See why security teams love us
Code-based runtime enable complete flexibility and performance for application protection at scale.











.svg)