Time to Exploit Has Reached -1 Days
According to Google's Threat Intelligence Group, the median time to exploit (TTE) for vulnerabilities has dropped to -1 days in 2024. This negative value indicates that attackers are now weaponizing vulnerabilities before vendors publicly disclose them or release patches—what was once the exception (zero-day exploitation) has become increasingly common.
Time-to-Exploit has dramatically decreased, reaching negative days in 2024
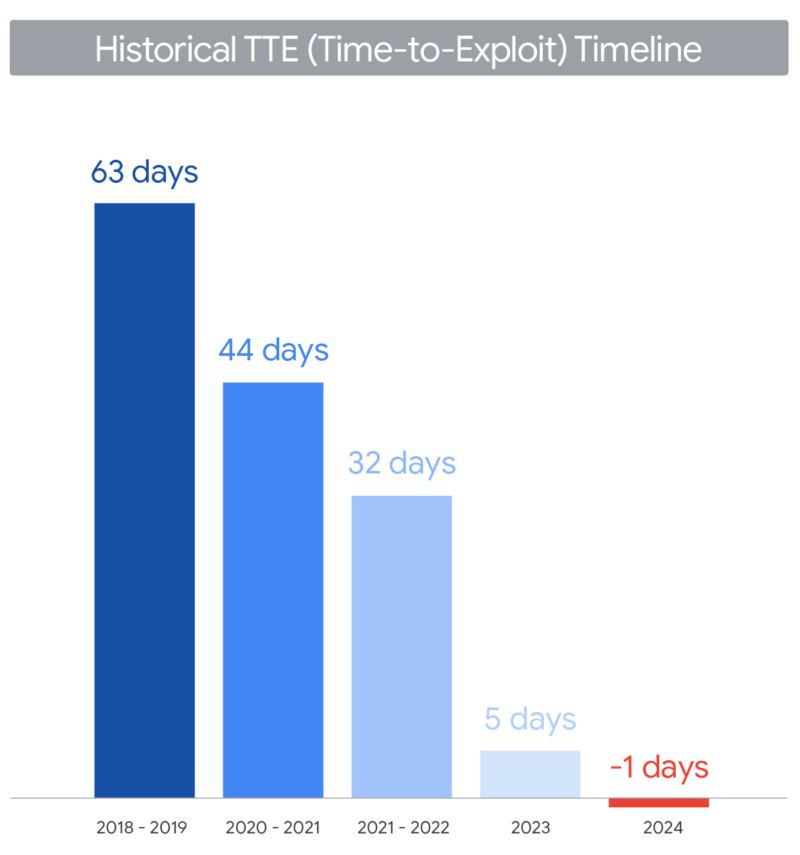
This represents a fundamental shift in the threat landscape. From 2018-2019, security teams had an average of 63 days to respond. By 2020-2021, this window shrunk to 44 days. The trend continued with 32 days in 2021-2022, then just 5 days in 2023. Now, we've crossed into negative territory.
Fast is the new normal
Conversations with security teams across industries reveal a consistent pattern: AI has compressed operational timelines without fundamentally changing the work itself. Threat investigation, incident response, and vulnerability management still require the same rigor, but the time window to execute these tasks has shrunk dramatically.
The Google TTE data quantifies this shift on the attacker side, but defenders face the same acceleration. Traditional MTTD (Mean Time to Detect) and MTTR (Mean Time to Respond) benchmarks that were acceptable 18 months ago are now inadequate. Security teams that operated on weekly sprint cycles are being forced to think in hours, not days.
Reducing Time to Defense (TTD)
The asymmetry between attack and defense has always been a fundamental problem in security, but AI has widened the gap. A large e-commerce customer we work with described it this way: "Every year my attackers are getting more sophisticated. It takes more effort to stop them and my existing tools get less and less effective."
The underlying issue is a scaling problem. Designing and deploying an effective defense requires more work than crafting an attack—you need to understand the threat model, implement detection logic, test for false positives, validate in production, and maintain the rule over time. AI accelerates the attack side of this equation without proportionally helping defenders who rely on manual workflows.
Most security tools still depend on click-ops interfaces, manual rule tuning, or professional services engagements to deploy new detections. These processes introduce latency that's acceptable when you have weeks to respond, but catastrophic when exploits are weaponized in hours or days. The teams winning this race are those who can iterate on detections with the same velocity that attackers iterate on exploits.
You can't prevent what you can't predict
Shift-left security and prevention-first strategies are essential—but they only protect you from known threats. The attacks that actually cause damage exploit your specific business logic in ways no amount of secure coding or perimeter defense can prevent.
Here's what we're seeing in production at Impart today:
- Attackers mass-ordering inventory to empty retail locations across the country, creating pure operational chaos
- Payment account draining timed precisely to post-event surges when your fraud team is already overwhelmed
- Coordinated buy-and-return schemes across dozens of stores that exploit subtle refund policy edge cases
- Bots systematically booking and abandoning appointment slots to game your availability algorithm
- Promo code stacking exploits that generate negative-price checkouts (yes, you pay them)
- Low-value purchases spread across hundreds of accounts—each below your fraud threshold—accumulating loyalty points at industrial scale
- Cart abandonment patterns designed to trigger your dynamic pricing discounts, then exploiting them at scale
Notice something? Every single one of these is a valid API call. Properly authenticated. Well-formed requests. Your SAST scanner sees no vulnerability because there isn't one in the code. Your WAF lets it through because the requests are legitimate. Your threat intel has nothing because these patterns are unique to how your application works.
You can't prevent what you can't predict. And you can't predict attacks on business logic you didn't know was exploitable.
What you need is continuous behavioral analysis of production traffic—systems that learn what normal looks like for your specific application, detect statistically significant deviations in real-time, and generate defensive responses automatically. Not in days. In minutes. AI that observes, hypothesizes, tests, and deploys detection logic faster than attackers can iterate.
AI-assisted defense needs guardrails
The shift toward treating security as code has accelerated dramatically. Security engineers are increasingly using AI coding assistants like Cursor, Windsurf, and GitHub Copilot to generate detection rules, WAF policies, and response playbooks at unprecedented speed. This democratization of security engineering is powerful, but it introduces new risks.
AI-generated security rules often contain subtle logic errors, produce false positives that disrupt production, or create blind spots due to incomplete threat modeling. Unlike traditional software bugs that cause visible failures, security rule errors fail silently—attackers exploit gaps that shouldn't exist, or legitimate users get blocked by overly aggressive policies.
What's needed is defensive infrastructure: automated testing frameworks that validate detection logic against known attack patterns and benign traffic, version control systems that track rule changes and enable rapid rollback, and continuous validation that ensures rules remain effective as application behavior evolves. The goal isn't to slow down security teams—it's to let them move faster with confidence that AI-generated defenses are production-ready.
Want to learn more about how our platform can help your team respond at machine speed? Contact us for a demo.
.svg)